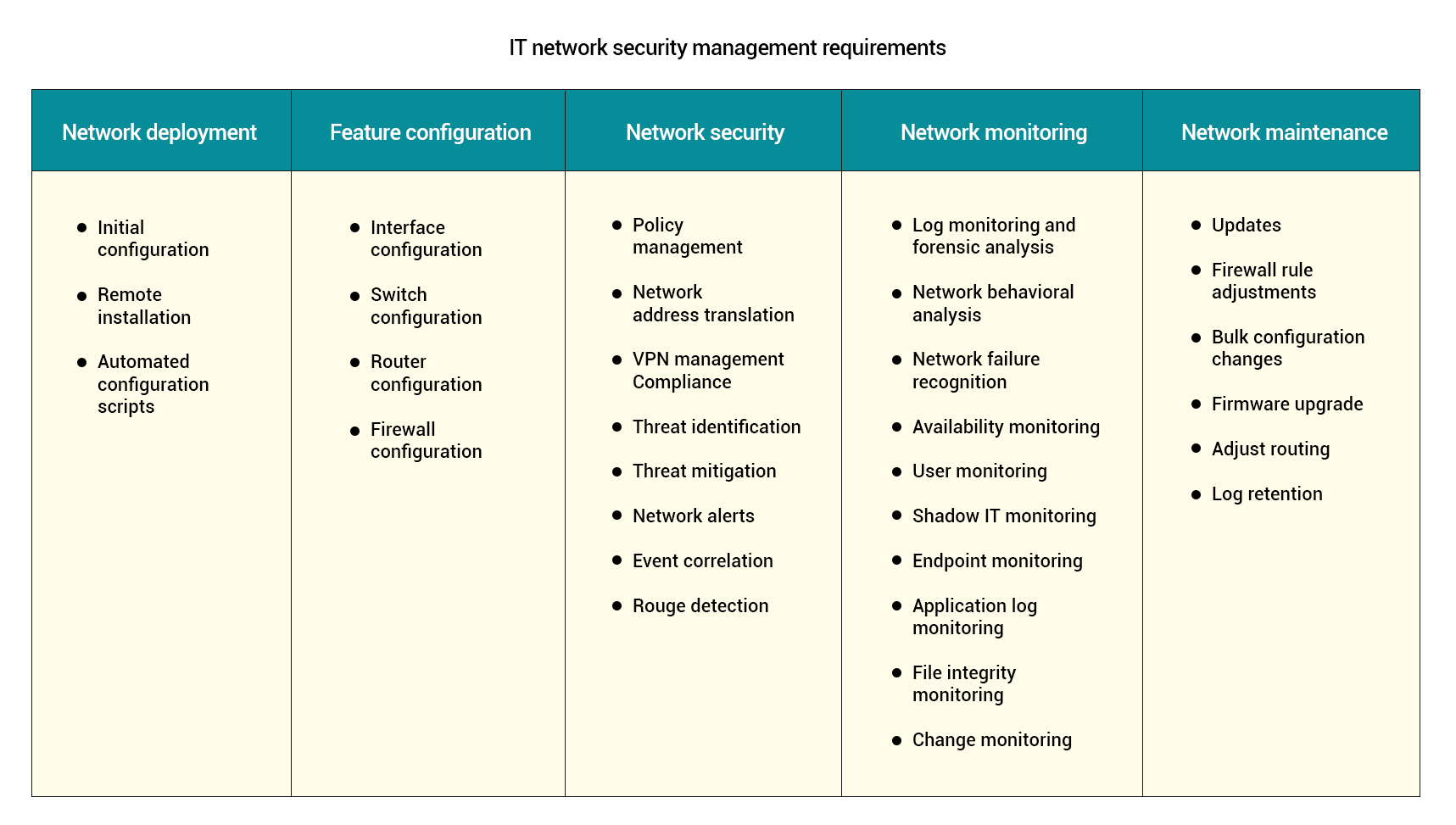
Network security management typically entails end-to-end management of the entire network security infrastructure of an enterprise. However, in this rapidly changing security ecosystem, there’s an inherent need for IT admins to be extremely agile to maintain an effective security posture.
Going beyond merely installing new security devices, security administrators need to address an ever-expanding matrix of users, locations, and applications; adhere to compliance; enable new services; optimize performance; ensure access controls and security mechanisms; and troubleshoot on demand. Any misconfiguration can make the network vulnerable to sophisticated threats and lead to non-compliance.
The following illustration depicts a scenario from a typical enterprise where the IT department needs to address network security management:
ManageEngine’s SIEM capabilities
ManageEngine ITOM solutions provide complete visibility into your network security infrastructure and help improve network security. The given ITOM solutions below offer a variety of security capabilities that help in network security management. Let’s take a closer look.
Firewall Analyzer: A firewall security management tool
ManageEngine Firewall Analyzer is a log, policy, and configuration management solution that offers the following network security management capabilities.
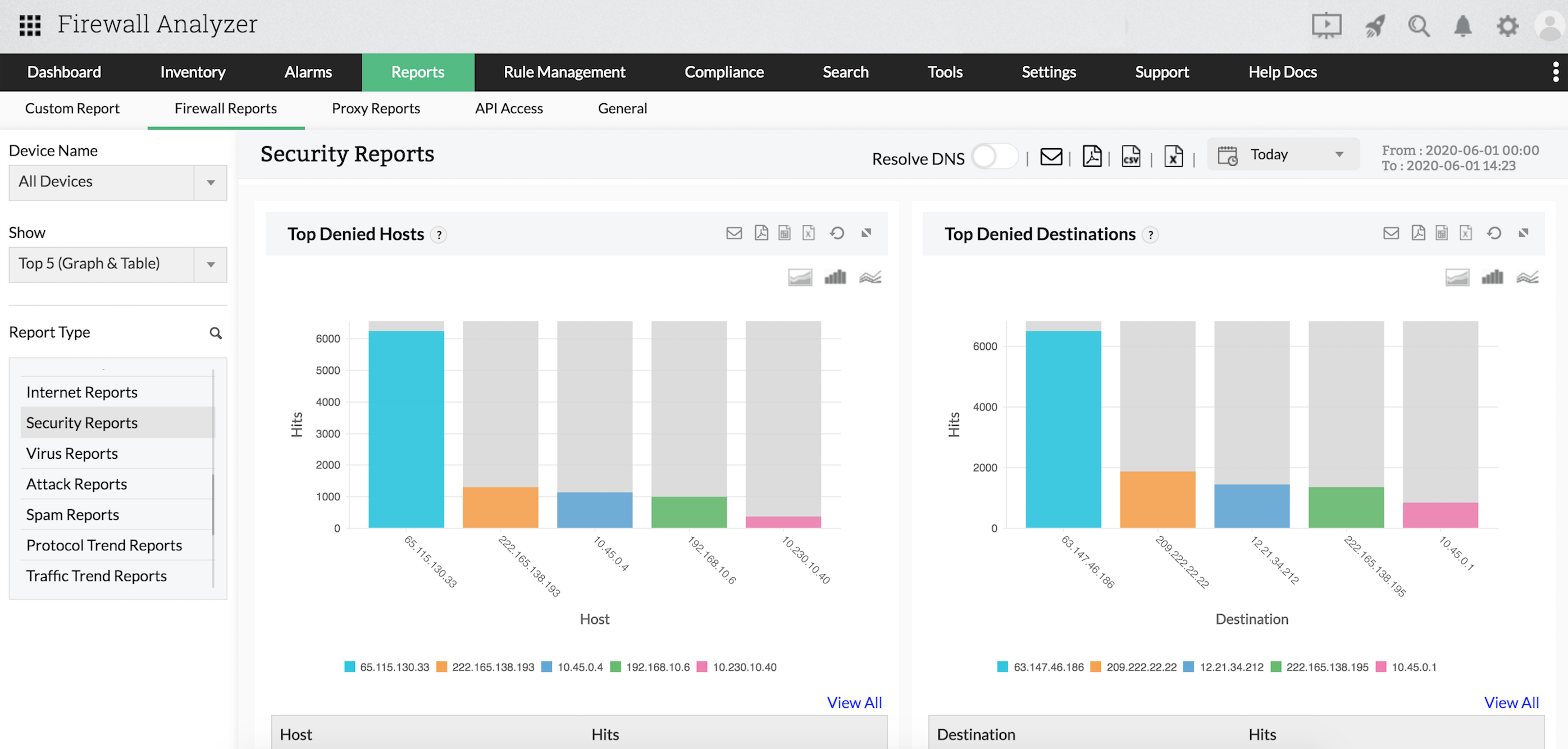
Firewall policy management: The heart of any firewall’s performance is its rules and policies. If not managed properly, these can leave the network vulnerable to attacks. Firewall Analyzer’s policy management helps you:
-
Gain visibility over your entire rule set.
-
Detect and record anomalies in redundancy, generalization, correlation, shadow, and grouping in your firewall.
-
Gain insight on how to improve performance by changing the rule order.
-
Automate firewall rule administration.
-
Determine if a new rule will negatively impact the existing rule set.
With these capabilities, you get complete control over the firewall policies, which helps you secure your network against attacks.
VPN management: As most enterprises move towards a flexible work model, a well-planned VPN strategy is extremely critical, both for employee productivity and security. With Firewall Analyzer’s security reports, you can easily identify network attacks and other malicious attempts made on your VPN users. On top of this, you can also administer rules directly into your firewall device to block suspicious IPs.
Change management: If your firewall configurations are not properly monitored and managed, your network may be left vulnerable to attacks. Firewall Analyzer fetches firewall configurations using the CLI or API from your firewall device and enables you to keep an eye on the changes being made to your network security infrastructure.
It also ensures that all the configurations and subsequent changes made in your firewall device are captured periodically and stored in the database. The configuration change management reports help you discover precisely who made what changes to the firewall configuration, when, and why. This report helps identify internal threats in your network.
Compliance management: Network security regulations are there for a reason. They help protect your business, your employees, and your customers. Failing to adhere to regulatory security compliance requirements can open you up to risks other than fines; it also poses a serious threat to your security posture.
Firewall Analyzer’s out-of-the-box compliance reports help you automate your firewall compliance for the following mandates: PCI DSS, ISO 27001, NIST, SANS, NERC-CIP. With these out-of-the-box reports, you can easily audit compliance on a regular basis, and secure your network from a compliance point of view.
Log analysis and threat identification: Firewall logs reveal a lot of information about attacks, viruses, suspicious hosts and destinations, infected devices, and suspicious user behavior. Firewall Analyzer fetches logs from the firewall and generates log reports to help you with:
-
Getting reports on possible security threats to the network including information on top denied hosts, denied protocols, and top security events generated.
-
Seeing in-depth information on virus attacks, hosts infected, and severity of the attack.
-
Monitoring user activity in the network, individual user-level bandwidth, and security anomalies.
-
Viewing detailed reports on possible network attacks including information on top attackers, top targets, and protocols used for the attack.
-
Seeing information on the spam activity in your network, top spam generators, top spam receivers, and top rules allowing spam.
-
Collecting and archiving proxy server logs, analyzing them, and generating useful corporate internet access information reports.
-
Generating reports based on URL categories for each firewall, including allowed and denied URLs. This is useful for monitoring and tracking internal threats in the network.
-
Generating reports for applications (like Skype and Yahoo Messenger) accessed through firewall devices and closely monitoring your shadow IT infrastructure.
With these reports, you can easily identify both internal and external threats in the network.
Log retention and forensics: You need to retain logs for a stipulated amount of time depending on which regulations you need to comply with. Below are some of the major compliance standards along with the retention period required for each regulation.
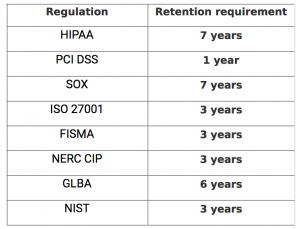
With Firewall Analyzer, you can retain logs in the database and set a time period for log retention. Different countries have different regulations for how long logs need to be stored for legal purposes. You should check with your legal team on which regulations your business needs to comply with.
Firewall Analyzer not only helps in log retention, but also in log forensics. With Firewall Analyzer’s smart search reports, you can easily search for specific historic security events and identify the specific log responsible for that event.
Network security alerts: Monitoring security and traffic-based firewall alerts are critical in identifying and preventing network threats in real time. Firewall Analyzer lets you set bandwidth and security-based triggers and notifies you directly via mail or SMS when exceeded.
Network Configuration Manager: A device configuration and compliance management tool
ManageEngine Network Configuration Manager is a network device configuration change and compliance management solution that offers the following network security management capabilities.
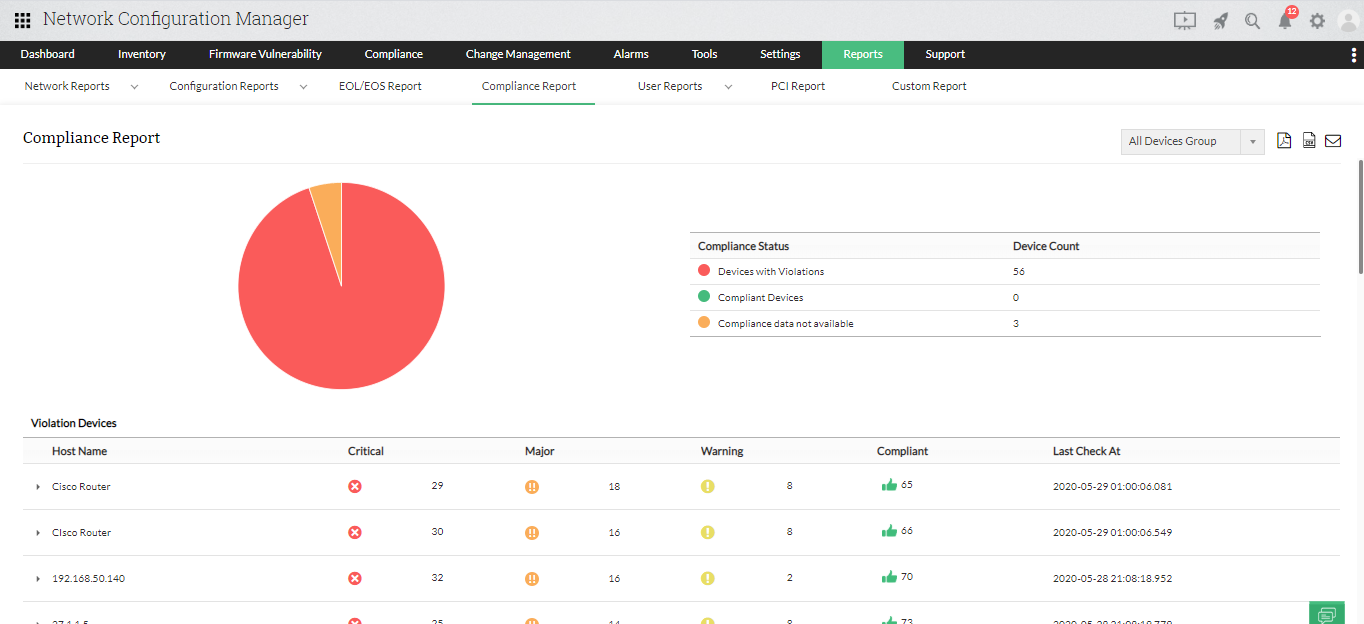
Configuration management: Using Network Configuration Manager, not only can you identify configuration loopholes by running compliance checks, but you can also push the required configuration change to a specific device and remediate violations.
You can also use Network Configuration Manager to push automated configuration scripts from a central location to network devices such as interfaces, switches, routers, firewalls, and VPNs located at a different location. This provides tremendous agility to make changes and rectify configuration issues across the entire network infrastructure.
Using Network Configuration Manager, you can also back up network configurations of devices individually or in bulk. You can choose to perform ad-hoc backups whenever required, or schedule them for devices in which configurations are regularly changed. Additionally, you can enable change detection for critical devices, and the solution will start detecting changes in real-time and trigger backups.
Change management: Keeping track of configuration changes is critical, especially when you’re trying to identify the root cause for network issues. Apart from maintaining a configuration change history, real-time notifications are also essential to enable admins to immediately review changes and take appropriate measures if the changes made are potential risks.
In critical devices like your firewalls and core routers, abrupt changes can come with huge risks. For such devices, you can enable a rollback mechanism which will ensure all changes made to those devices’ configurations will immediately be reverted.
Compliance management: With the increasing security threats to network resources, enterprises are required to follow standard practices, and execute internal/external security policies to remain compliant with the latest industry standards.
Network Configuration Manager enables network admins to run compliance checks and generate out-of-the-box compliance reports for CiscoIOS, HIPAA, SOX, and PCI DSS industry standards. Auditing these reports on a regular basis can help identify configuration loopholes across all network devices.
Risk mitigation: Changes in network configurations, if not done carefully, can create security vulnerabilities. If these changes are applied to multiple devices at the same time, then fixing them manually would be time-consuming. Network Configuration Manager enables you to fix such vulnerabilities in multiple devices using configlets.
Configlets are configuration script templates that you push to individual or several devices simultaneously. Network Configuration Manager comes with a set of default configlets for common network tasks and also allows you to create custom configlets to serve your specific requirements. So, whenever a security issue has been detected, a simple configlet execution can fix it and save your network from a possible attack.
NetFlow Analyzer: A network behavior analysis and bandwidth management tool
NetFlow Analyzer is a comprehensive bandwidth monitoring and network traffic analytics solution. In addition to bandwidth and traffic management, NetFlow Analyzer can detect anomalies and offers the following network security solutions.
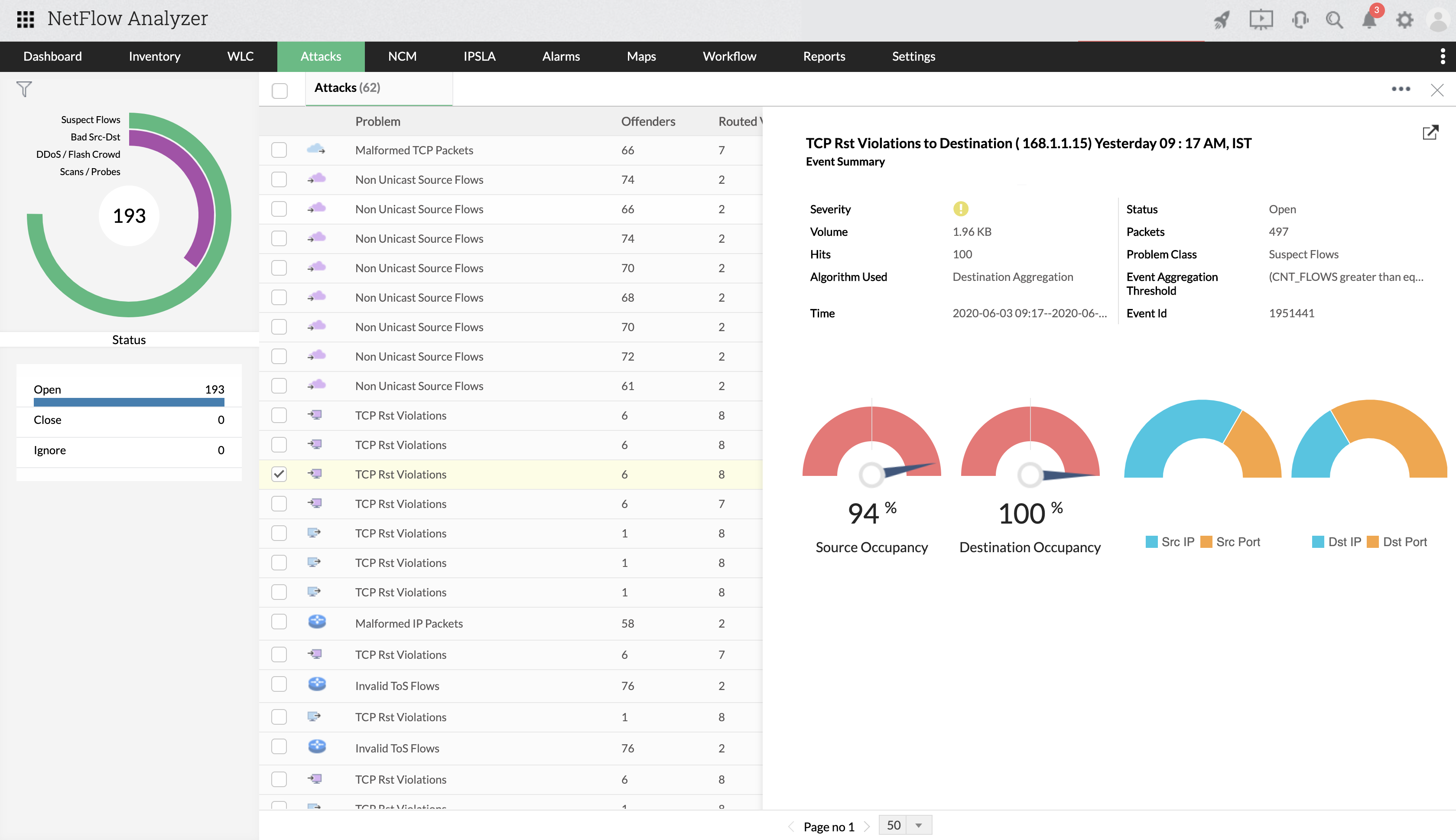
Network forensics: While network forensics is primarily used to detect malware and attacks, NetFlow Analyzer’s forensics report helps detect network anomalies while keeping track of the overall performance of your network and bandwidth.
By closely monitoring and analyzing network behaviour trends, it identifies irregularities in your network that are otherwise neglected. Using raw data to derive its detailed analysis, NetFlow Analyzer helps you get to the root cause of network issues and troubleshoot them before they evolve into a threat.
Network behavioral analysis: Network security involves much more than having a high-end firewall in place. While a complete network security system ideally includes a firewall, an intrusion detection system, and a behavior analysis system that all complement one another, the network behavior analysis system is often disregarded, leaving the network unguarded against unknown threats that may have surpassed your firewall.
NetFlow Analyzer uses network behavior analysis for real-time threat detection and network surveillance. It plays a major role in identifying network traffic patterns and streamlining security analysis.
Threat detection: NetFlow Analyzer’s security analytics module helps identify and classify attacks in the network. The Advanced Security Analysis Module (ASAM) has a specially built Continuous Stream Mining Engine that performs network behavioral analysis to sense zero-day intrusions, suspicious flows, unknown worms, DDoS attacks, scans, probes, and various other external and internal threats before they bring the entire network to a standstill.
It helps identify, classify, and group issues into events based on severity and type, and further dissects each event to analyze source, destination, conversation, target, and offender details.
Security alerts: NetFlow Analyzer has a set of pre-defined algorithms and thresholds based on which security attacks and events are classified. These existing criteria can be customized to create alert profiles that will notify you via email and SMS every time there is a violation.
OpUtils: IP address and switch port management
OpUtils is IP address and switch port management software that is geared towards helping engineers efficiently monitor, diagnose, and troubleshoot IT resources. OpUtils offers the following network security management capabilities.
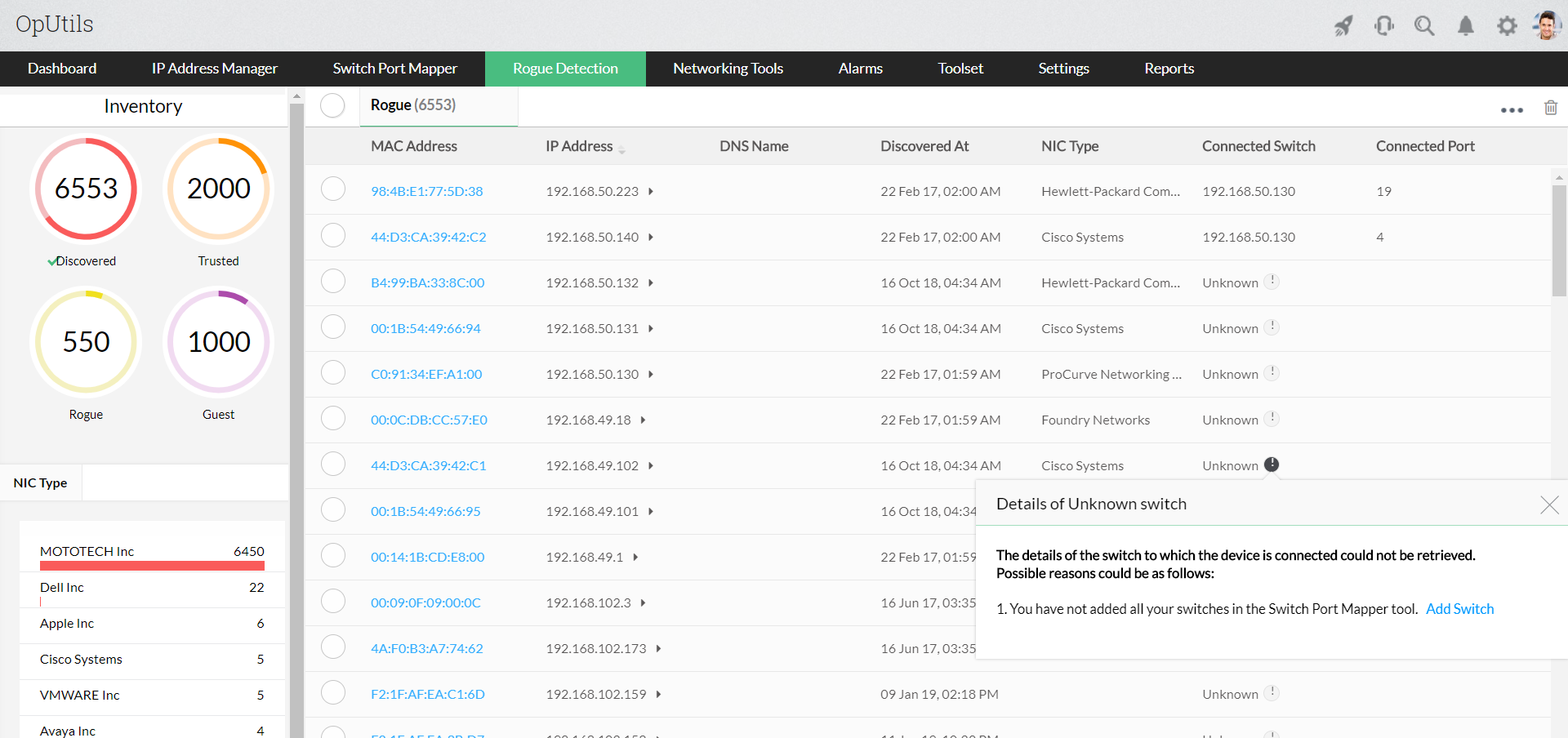
Rogue device detection: With a bring your own device (BYOD) policy allowing a number of unverified devices to connect with your network, leaving them unmanaged may pose a security vulnerability. Having an effective solution in place to manage and monitor these devices, their pathways, and connected endpoints helps you secure your network from unauthorized access.
OpUtils’ Rogue Detection feature continually scans and lists all the newly discovered and unmanaged devices in your network. It allows you to verify and mark these devices as rogue in the case of unauthorized devices. By combining its capabilities with those of the Switch Port Mapper, it displays the port to which the rogue device has connected. These endpoints can be blocked or unblocked within OpUtils, helping you block access to your network.
In situations where temporary access to network resources is required, devices can be marked as “guests,” which lets you assign a time limit within which the devices can access the network. Verified devices can be given the “Trusted” status, allowing them complete access to your network resources.
Instant alert notifications: OpUtils’ Rogue Detection system scans your network in real-time, monitoring all the devices accessing your networks, and alerts you instantaneously whenever an unauthorized access to your network is detected. You can view these alerts via your console, email, or SMS.
Apart from these individual solutions, ManageEngine’s ITOM suite also has an integrated IT operations management solution, OpManager Plus, in its product portfolio.
OpManager Plus eliminates the need for multiple monitoring tools and is packed with advanced IT operations management capabilities for monitoring networks, servers, IP addresses, and switch ports; managing bandwidth and network configurations; and analyzing firewall logs.
Download a free trial of ManageEngine’s suite of ITOM products, and leverage this powerful, integrated solution offering a unified approach to network security management to rid your network security infrastructure of blind spots.
The post Tackling your network security challenges using ManageEngine ITOM solutions appeared first on ManageEngine Blog.
*** This is a Security Bloggers Network syndicated blog from ManageEngine Blog authored by Mouli Srinivasan. Read the original post at: https://blogs.manageengine.com/network/2020/11/02/network-security-management.html
"network" - Google News
November 02, 2020 at 08:28PM
https://ift.tt/3oQqV1J
Tackling your network security challenges using ManageEngine ITOM solutions - Security Boulevard
"network" - Google News
https://ift.tt/2v9ojEM
https://ift.tt/2KVQLik
Bagikan Berita Ini














0 Response to "Tackling your network security challenges using ManageEngine ITOM solutions - Security Boulevard"
Post a Comment